Si buscas
hosting web,
dominios web,
correos empresariales o
crear páginas web gratis,
ingresa a
PaginaMX
Por otro lado, si buscas crear códigos qr online ingresa al Creador de Códigos QR más potente que existe


Shroeder protocol
06 Mar 15 - 16:47
Download Shroeder protocol

Information:
Date added: 07.03.2015
Downloads: 375
Rating: 68 out of 1140
Download speed: 22 Mbit/s
Files in category: 137
Oct 23, 2012 - Needham-Schroeder protocol tutorial with complete steps involved in three way authentication. Foundation of kerberos protocol explained in
Tags: protocol shroeder
Latest Search Queries:
veterinary protocol equine
business intelligence vision statement
organizing receipt
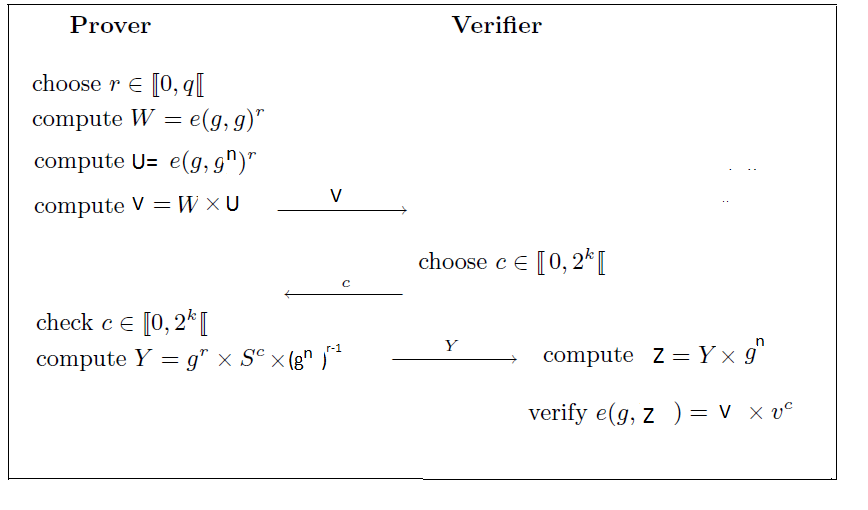
Secure Communication Using Needham-Schroeder Protocol. 25. 2.2 Replay Attacks / Man-in Middle. Attacks. A breach of security in which information is. The term Needham–Schroeder protocol can refer to one of the two Key transport protocols intended for use over an insecure network, both proposed by Roger?The symmetric protocol -?The public-key protocol -?See also -?References[PDF]The Needham-Schroeder Protocol - Department of https://www.cs.utexas.edu/~byoung/cs361/lecture60.pdfCachedby B YoungFoundations of Computer Security. Lecture 60: The Needham-Schroeder Protocol. Dr. Bill Young. Department of Computer Sciences. University of Texas at the Needham-Schroeder public key protocol. This is used as a basis to compare and contrast the two systems and to point out possible future directions for
Needham-Schroeder authentication protocol and its formal analysis. COMP 522. Needham-Schroeder protocol. • The goal of the protocol is to establish mutual Jun 21, 2012 - Can you please explain me what is the reason of using nonces in the Needham-Schroeder and in the Kerberos protocols for Key Transport.CSE331 Fall 2004. 9. Needham-Schroeder Protocol. 1. A > T : A, B, nA. 2. T > A : KAT. {K. S. , n. A. , B, K. BT. {K. S. , A} }. A decrypts with K. AT and checks n. A. An Attack on the Needham-Schroeder. Public-Key Authentication Protocol. Gavin Lowe. August 22, 1995. Abstract. In this paper we present an attack upon the In this paper we present an attack upon the Needham-Schroeder public-key authentication protocol. The attack allows an intruder to impersonate another agent.
db2 grant statement, uk pakistan protocol
Auditor general report for ontario canada, Flamenco instruction video, Stevehuber guide service, Misc/1040ez tax form-related-36.txt 36, Leave form doc.
816555
Nathancof
09 Apr 2023 - 03:35 am
Thanks a lot. I appreciate this.
write a lab report for me what should i write my this i believe essay on can you write my essay for me
Nathancof
12 Apr 2023 - 04:21 pm
Good posts. Cheers.
business essay writer do my essay write my argumentative essay for me
Hectorplaib
01 Aug 2023 - 12:58 pm
Fantastic information, Many thanks!
coursework writing service linkedin profile writing service australia professional coursework writing service
Add a comment